For years, many businesses have simply configured a few settings in Microsoft Active Directory Password Policy and felt good about their password policy security. However, traditional password policy settings are no longer enough protection for user accounts housed in Active Directory.
A robust password policy is the lifeblood of password security. Organizations who want to adequately protect their business from the dangers of credential theft and data breach due to compromised credentials must give due consideration to a robust password policy.

Best Principles and Practices of a Good Password Policy
Let’s look at the top five tenets of a good password policy and see what password policy features your organizations should look to enable.
1. Account lockout threshold
The account lockout threshold is a legacy setting. However, it is still noted as a password policy setting that holds value in protecting accounts from compromise. So, what is the account lockout threshold, and how does it help to protect end-user accounts from compromise?
The account lockout threshold is a password policy setting that determines the number of failed login attempts before the Active Directory user account is locked out. The NIST Special Publication 800-63B Digital Identity Guidelines document states the following:
“Verifiers SHALL implement a rate-limiting mechanism that effectively limits the number of failed authentication attempts that can be made on the subscriber’s account as described in Section 5.2.2.”
Locked accounts can be a tremendous burden on helpdesk teams already stretched thin due to the shift to the remote workforce. Implementing a self-service system for end-users to reset passwords significantly reduces the helpdesk’s burden and gives end-users quicker resolution.
2. Minimum password length
The minimum password length is a password policy setting that defines the minimum length of the password that end-users can choose. The length of a password contributes to the password’s strength. Therefore, determining an Active Directory password length helps ensure users create passwords with the minimum acceptable length. NIST recommends that passwords that are user-chosen have a minimum length of 8 characters.
Organizations can also implement solutions to reward users who choose longer passwords with more extended thresholds before requiring a password change. Length-based aging is a concept that can promote users choosing longer passwords, increasing security.
3. Breached password protection
Attackers today are making use of new techniques to compromise end-user accounts in Active Directory. They include using databases of breached passwords found on the dark web and using these “breached passwords” in credential stuffing or “alphabet” style attacks on user accounts.
When you think about it, most end-users think very similarly when it comes to their passwords. We all try to set passwords that meet the complexity guidelines set by the system administrator while, at the same time, are easy to remember. Unfortunately, this similarity in how we think and create passwords can lead to password compromise.
Two unrelated users who work in different organizations may think of the same password. What happens when the first user’s password is leaked in a data breach? Although not directly breached, the second user’s password is now exposed since it is identical to the breached password. If an attacker gets hands on the list of breached passwords and uses this list on the second organization, the likelihood of compromising the second user’s account is high. This scenario illustrates why breached password protection is now so important. It is also why leading cybersecurity guidance from authorities such as NIST has changed its stance on period password changes or password aging. Note the following:
“Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically). However, verifiers SHALL force a change if there is evidence of compromise of the authenticator.”
Notice in the above. NIST is recommending a forced password change ONLY when there is evidence of compromise. This guidance implies some form of breached password protection. Additional guidance from NIST includes the following:
“When processing requests to establish and change memorized secrets, verifiers SHALL compare the prospective secrets against a list that contains values known to be commonly-used, expected, or compromised. For example, the list MAY include, but is not limited to:
- Passwords obtained from previous breach corpuses
- Dictionary words.
- Repetitive or sequential characters (e.g. ‘aaaaaa’, ‘1234abcd’).
- Context-specific words, such as the name of the service, the username, and derivatives thereof
If the chosen secret is found in the list, the CSP or verifier SHALL advise the subscriber that they need to select a different secret, SHALL provide the reason for rejection, and SHALL require the subscriber to choose a different value.”
The bottom line for modern password policies – they need to enforce breached password protection. Breached passwords can easily compromise high-level accounts, even if the passwords are seemingly complex.
4. Custom password dictionary
Another modern characteristic of a good password policy is a custom password dictionary. Password dictionaries are similar in purpose but different than breached password protection. Password dictionaries contain disallowed passwords that end-users cannot use. It allows an organization to customize the passwords they do not allow, such as variations of the business name in the user’s password.
Attackers will often use variations of the business name and other words associated with an organization to “think like the user” and guess passwords they may have chosen to use. A custom dictionary creates what is known as a password filter in Active Directory that filters user’s passwords and prevents users from setting a password that exists in the list.
Active Directory lacks an easy way to implement password filters and requires in-house development skills to produce the necessary .dlls to implement the password filter correctly. In addition, Azure Active Directory password filtering is also limited in its feature set and functionality. As a result, organizations require third-party solutions to implement password filtering to protect against commonly used passwords.
5. Password history
Keeping a history of passwords used by end-users prevents a user from using the same password quickly. In other words, you do not want a user to change their password, and then at the next interval, they change the password back to what it was before. Therefore, the password history setting specifies the number of passwords “remembered” that users cannot use when changing their passwords.
Here again, native Active Directory functionality is limited. For example, while it can remember passwords that have been used, it does not effectively block incremental passwords (i.e., simply adding a different number to the end). A third-party solution is required to block against incremental password use in the environment.
Modern password policies require a third-party solution
Active Directory does not have the native functionality to implement breached password protection. In addition, while custom password filters can be used and implemented in Active Directory using a password filter .dll, it requires development expertise and continual maintenance. As a result, it becomes clear that it requires a third-party solution for organizations that want to meet password policy security challenges.
Specops Password Policy is one such solution, a robust option that allows organizations to meet the top 5 tenets of a good password policy, as discussed, and many others. In addition, Specops Password Policy integrates with Active Directory Group Policy settings. So, it fits in seamlessly with existing policies that organizations have in place.
The two password protections that are either non-existent in Active Directory or hard to do (breached password protection and custom dictionaries) are protections Specops Password Policy can help you implement in just a few clicks.
The Breached Password Protection module in Specops Password Policy provides an easy way to implement breached password protection that goes beyond leaked lists. Specops Breached Password Protection blocks the use of over 2 billion compromised passwords, including ones used in real attacks today or are on known breached password lists, making it easy to comply with industry regulations such as NIST or NCSC.
Our research team’s attack monitoring data collection systems update the service daily and ensure networks are protected from real-world password attacks happening right now. The Breached Password Protection service blocks these banned passwords in Active Directory with customizable end-user messaging that helps reduce calls to the service desk.
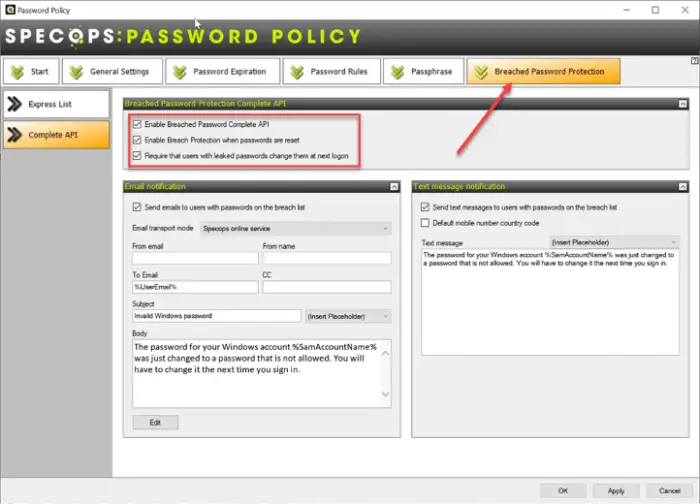
Specops Password Policy Breached Password Protection can be used via an API or an express downloadable list
The custom dictionaries option with Specops Password Policy provides an easy way to add custom dictionaries to protect against targeted password attacks that may contain your organization’s name or other sensitive phrases.
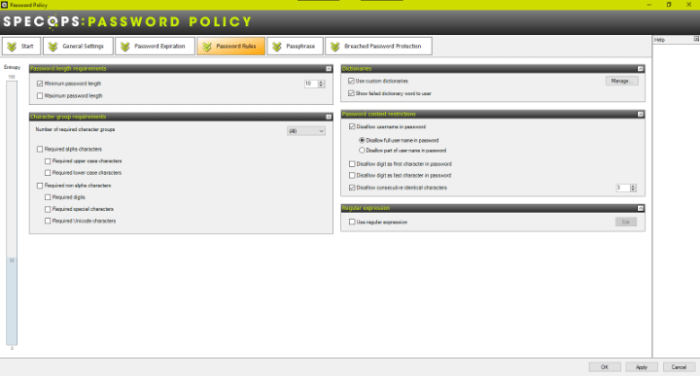
Specops Password Policy custom dictionaries
What additional features are found in Specops Password Policy?
- Informative client messaging so end-users understand why their password change attempt fails
- Dynamic feedback at password change with the authentication client provided by Specops
- Password expiration based on the length of the password
- Customizable email notifications
- Block common password components such as user names, display names, specific words, consecutive letters, incremental passwords, etc
- GPO-based targeting
- Support of using passphrases as passwords
- Regular expression capabilities
Wrapping it Up
Password policy requirements are changing based on the ever-increasing cybersecurity threats. This change is seen in new password policy guidance from NIST and others. It is no longer enough to use the built-in password policy settings found in Active Directory. Businesses today need to protect against threats such as breached passwords.
Today, companies need to use a third-party solution to augment the capabilities found in Active Directory to meet the top 5 tenets of a good password policy. Specops Password Policy is a solution that allows organizations to implement password filters using password dictionaries and breached password protection. In addition, it includes many other great features not found in Active Directory, such as length-based password aging.
Learn more about Specops Password Policy or start a free trial here.
Leave a Reply