Many different types of password security issues can creep into an organization’s Active Directory environment. For example, end-users are notorious for using easily guessed passwords that meet the criteria for complex passwords and are not secure. An example is using the password, P@$$w0rd123. It meets the technical definition of complex but is easily hacked.
In addition, end-users may even choose passwords that are found on breached password lists like HaveIBeenPwned.com, and more. Due to modern cybersecurity threats, finding breached passwords in Active Directory must be a priority. However, there is no native way in Active Directory to identify breached passwords.
Luckily, there is a way to use PowerShell to find breached passwords, here’s how.
Why breached passwords are so dangerous?
A well-meaning IT admin might conclude that even if a user in my organization chooses a password found in a breached password database an attacker has access to, it isn’t the same user account. It is true. An attacker must match the valid user account with the right password before it is technically “correct.” However, attackers can use known passwords in specific attacks to “find” user accounts with that particular password.
In password spraying attacks, hackers can use a few passwords and spray these passwords at a large number of accounts to see if any of the passwords are found to work. Attackers often use breached password lists of known passwords that users have chosen before.
The problem is that we as humans tend to think alike. For example, suppose one user thinks of a specific password that uses particular transformations in characters and a certain combination of special characters. In that case, there is a good possibility another user in a completely different organization will think of the same password. Attackers know this, and using previously breached passwords against other user accounts proves effective.
Also, most end-users are juggling access to multiple systems and solutions, both on-premises and in the cloud. All of these require a password. In addition, to easily guessed passwords, hackers know that users are using the same password for multiple accounts. If one password is compromised, all systems using that password are compromised.
Experts Study on Password Data Breach
A 2019 Google study with a Harris Poll found that 13 percent of people reuse the same password across all accounts, and a further 52 percent use the same one for multiple (but not all) online accounts. Only 35 percent use a different password for every account.
Compromised credentials are a highly effective way that cybercriminals can attack business-critical data. If legitimate credentials are found to gain access to a critical system, attackers can “go right through the front door” with little effort.
In the 2021 Data Breach Investigations Report published by Verizon, it was stated:
“Phishing continues to walk hand-in-hand with the use of stolen credentials in breaches as it has in the past. Admittedly, we expected to see an increase here due to a larger remote workforce.”
In the same report, it points out that credentials are one of the most desirable types of information for an attacker:
“As we have pointed out in previous reports, Credentials remain one of the most sought-after data types….”
The credential compromise increases the cost of data breach events. According to the IBM Cost of a Data Breach 2020 report:
“Stolen or compromised credentials were the most expensive cause of malicious data breaches. One in five companies (19%) that suffered a malicious data breach was infiltrated due to stolen or compromised credentials, increasing the average total cost of a breach for these companies by nearly $1 million to $4.77 million.”
How to find breached passwords with PowerShell
Since Active Directory has no built-in means to find breached passwords or any built-in breached password protection, businesses must use other means to find breached passwords that are in use. One way that companies can discover breached passwords in Active Directory is using PowerShell.
PowerShell is a powerful scripting language that is freely available in modern Windows Server versions and can easily be used to audit Active Directory passwords to discover breached passwords in use by end-users. Let’s see how.
As an example of a PowerShell module that can find breached passwords, the National Counterintelligence and Security Center (NCSC) has released a script called pwauditor which makes use of a module called DSInternals.
First, download the .zip file or clone the repo found here on GitHub.com.
Next, unzip the file to a folder of your choosing. After downloading this script, you will need to install the DSInternals module. You can do that with this command:
Install-Module -Name DSInternals -RequiredVersion 2.22
Adding the DSInternals PowerShell module
When you install the module, it will place it in the following directory:
C:\Program Files\WindowsPowerShell\Modules\DSInternals\2.22
Copy the parent “DSInternals” directory into the unzipped directory for the pwauditor download. Also, you will need to place all the files in the 2.22 directory inside the parent DSInternals directory. The structure of the directory will look like this:
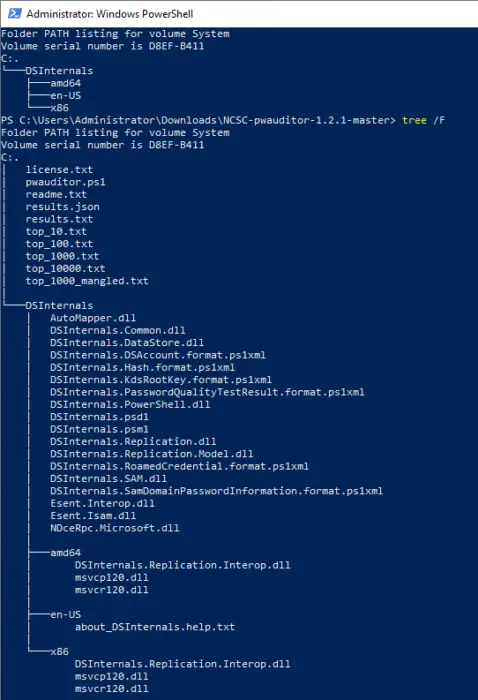
Tree view of the pwauditor and DSInternals utilities combined in same folder
Now, run your command as follows:
.\pwauditor -DC dctest1.neptune.local -NC "dc=neptune,dc=local" -blacklists top_10.txt,top_100.txt,top_1000.txt,top_10000.txt,top_1000_mangled.txt -organisation NEPTUNE
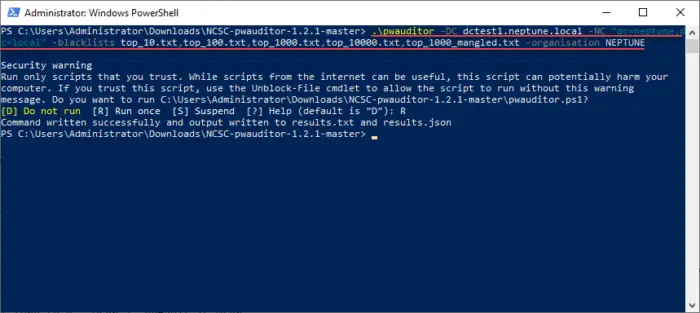
Running the pwauditor command
Running the command produces a “results.txt” and a “results.json” file. Both display the same information.
You are able to see how many passwords contained in the breached password lists were found.
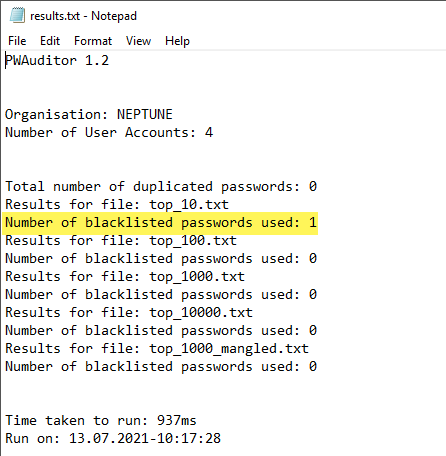
Viewing the results.txt file
The downside to the results file is that it only tells you that it found the password in the user accounts searched, but it does not tell you which user account is affected. In addition, just using simple password lists means organizations are leaving themselves vulnerable. Checking accounts against large breached password databases, in conjunction with real-time protection against passwords used in live brute force attacks is necessary to ensure password security among modern cybersecurity threats.
Read: Password Cracking attacks, methods, prevention
An easier approach than PowerShell is using Specops Password Auditor
While PowerShell can certainly provide visibility missing in native Active Directory capabilities, it can be cumbersome to use and maintain. You may also find open-source resources such as the NCSC script. However, these types of resources may not be actively supported, could be buggy, and may not give the visibility to breached passwords needed.
Specops Password Auditor is a freely available tool that allows finding breached passwords in Active Directory. It quickly scans the environment for breached passwords from our combined list of 750M+ known breached passwords and can show you admin entropy, repeated passwords, policy compliance and so much more.
Note the following output from a run of Specops Password Auditor. You quickly have visibility to breached passwords, among others. Furthermore, it leaves no question about the account(s) that are using breached passwords.
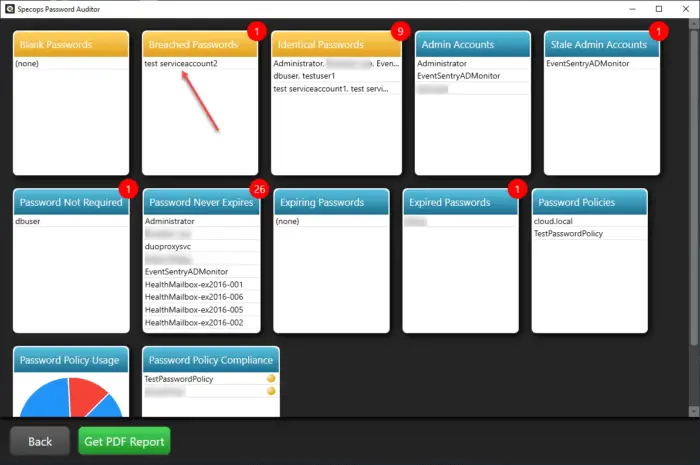
Specops Password Auditor displaying results from a scan
Wrapping it up
Finding breached passwords in Active Directory is a priority for organizations looking to bolster their account security. However, Active Directory does not natively have a feature to gain visibility to breached passwords used in the environment. Using various PowerShell tools, as shown above, can help to have visibility to breached passwords despite a few challenges of its own, including lifecycle management and support.
Luckily, Specops Password Auditor is a free and simple tool that allows quickly seeing any accounts in the environment using breached passwords and other security concerns.