When it comes to privacy and security, there is no compromise, but when it comes to choosing which software or service should be picked up, there is a lot of confusion. As cloud computing and virtualization become integral parts of business operations and development enterprises are increasingly dependent on cloud-based applications to deliver critical business-critical services and value. While these applications help companies retain control and maintain their independence from the cloud, the security and privacy of these applications are critical. That’s where services such as Hysolate come into the picture. It enables organizations to isolate risk, sensitive activities, applications, and data from the risk of getting tampered with or infected from 3rd party malware attacks. It also practices safe browsing redirection to protect the workspace from sensitive websites.
Hysolate Review
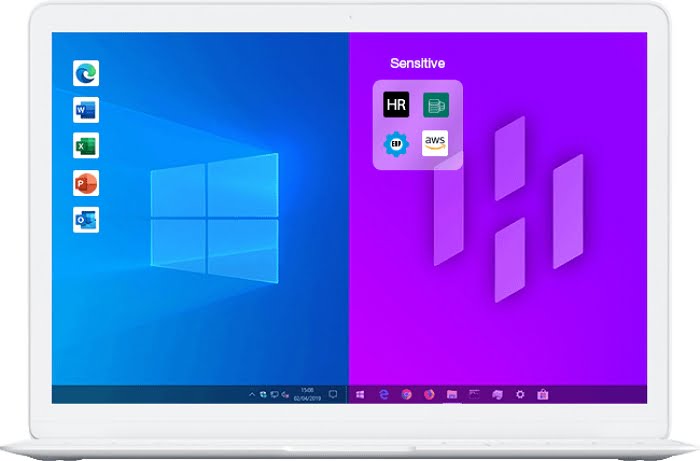
Hysolate Features and why it’s required for security and privacy
There are already a lot of solutions out there, then what makes Hysolate different. Let’s check out the list of features that will help us understand.
Full isolation: Hysolate ensures that all sensitive information is completely isolated from the network and avoids open connectivity to the internet. Hysolate’s unique architecture isolates data, applications, or cloud services for an extra level of endpoint protection.
VM-based isolation: Using Hysolate, you can “split” the user’s device into two isolated environments. It ensures that if you don’t trust the device, or the OS, or the application, or the network, or the cloud, you can be sure.
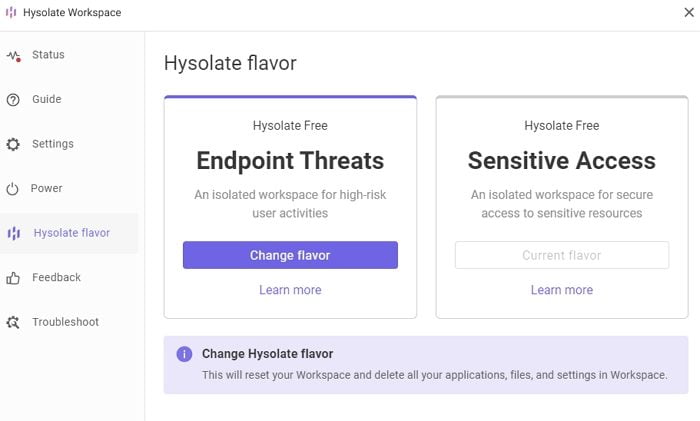
Keeping Workspace Safe:
The VM ensures that any sensitive application or website we want to protect is automatically opened in the secured VM environment. This way no malicious software on the endpoint can damage the sensitive information. It also prevents malware from keylogging or capturing applications and data, and blocks screenshots of sensitive information and data.
Encryption: Last but not least, the service offers state-of-the-art security using data encryption in transit and at rest. The Hysolate software is designed to protect your data and can secure all terminals.
Use Cases for Hysolate
- Isolate Access to Sensitive Applications and Data: It lets you create multiple isolated zones to control access to sensitive data, websites, applications, or cloud services from known or unknown malware.
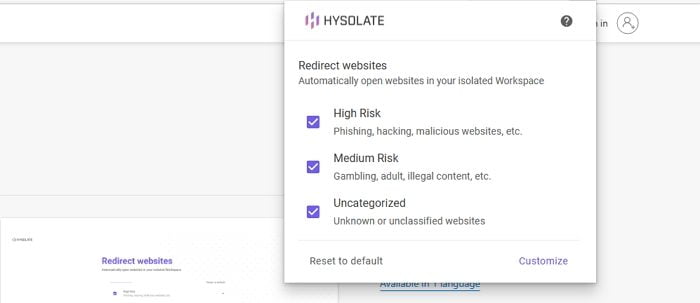
- Improve Employee Productivity with IT-Freedom: It protects your employees from the dangers of social media, IM, peer-to-peer, personal email, malware, and ransomware by isolating these activities and suspicious websites from the work environment. Hysolate clients are productive because they can access any website application without being blocked from their working endpoint without imposing any risk to company assets.
Other use cases include extending Zero Trust to the endpoint, Isolating privileged access to corporate systems & data and isolating contractors’ and offshore teams remote access.
Enterprise Use of Hysolate
Hysolate makes it easy to deploy the VM specifically to enterprises without taking much time. It also ensures to support all Enterprise policy with support and SLA.
Data Capture Restriction: Automatic redirection of websites, docs, apps, and USBs makes sure that a user’s sensitive data cannot escape from the organization. The user is not even allowed to look at a website not approved by the enterprise. It also supports advanced security policies such as restrictions on clipboards, printers, screenshots, keylogging, and the ability to capture data.
External device policy management: Hysolate’s flexible policy engine ensures that the user of external devices, who may not be your typical corporate user, complies with the company’s policy. If someone tries to use an unauthorized device to access the data, the Hysolate software encrypts all the data on the devices before allowing access to it. It makes it very difficult for anyone to use an external device on the system.
IdP integration and SAML-based SSO: It ensures a smooth experience for users accessing Hysolate applications through a third-party identity provider. It is important to have this in place for the same-domain cookie restrictions to work properly
Fine-grained networking policies: You can configure business-critical applications in an isolated network and control access to sensitive data. It ensures the protection of cloud services with granular corporate policies.
Comprehensive application bundling options and granular file policy settings give you the control and flexibility to deploy Hysolate across your infrastructure.
Hysolate Pricing & Demo
One of the best parts of Hysolate is that it is easy to install and can transfer between regular and secure mode with the click of a button. It not only saves time but makes it suitable for both technical and non-technical people. On top of this, if you are looking for Windows VM, you don’t have to buy any license as the cost is included.
That said, the company offers users to evaluate their service using a free demo. All you need is Windows 10 or Windows 11 Pro/Enterprise with 8GB RAM, SSD, Intel Core i5 or higher (or an AMD equivalent). Once you fill in the form, a link will be sent to download it, and then you can further test it. Make sure to use a company email account for the demo.
Once installed, you will be able to experience the secure setup on the same computer where your work and personal file reside. The extensions for browsers make sure data is safe from websites that can steal data.
Its heterogeneous configuration settings are nothing but a gateway switch to restart workspace, switch between sensitive access, and troubleshoot problems etc.
Hysolate - FREE
-
Data Integrity and Privacy - 95%
95%
-
Functionality & UI - 92%
92%
-
Location Oriented Setup - 92%
92%
-
Enterprise Level configuration - 95%
95%
-
Remote Device Data Protection - 95%
95%
Leave a Reply